Virtual Machine In Web Browser
Share this story.ATLANTA—Microsoft has announced that the next major update to Windows 10 will run its Edge browser in a lightweight virtual machine. Running the update in a virtual machine will make exploiting the browser and attacking the operating system or compromising user data more challenging.Called Windows Defender Application Guard for Microsoft Edge, the new capability builds on the virtual machine-based security that was first introduced last summer in Windows 10. Windows 10's Virtualization Based Security (VBS) uses small virtual machines and the Hyper-V hypervisor to isolate certain critical data and processes from the rest of the system.
Browserling did a custom cross-browser testing solution for UK's National Health Service. Our application needs to operate in complicated sub optimal technological environments where legacy software is popular and unrealistic expectations to meet modern standards impose unsurpassable barriers to implementation.
The most important of these is Credential Guard, which stores network credentials and password hashes in an isolated virtual machine. This isolation prevents the popular MimiKatz tool from harvesting those password hashes. In turn, it also prevents a hacker from breaking into one machine and then using stolen credentials to spread to other machines on the same network.The Edge browser already creates a secure sandbox for its processes, a technique that tries to limit the damage that can be done when malicious code runs within the browser. The sandbox has limited access to the rest of the system and its data, so successful exploits need to break free from the sandbox's constraints.
Browser Based Virtual Machine
Often they do this by attacking the operating system itself, using operating system flaws to elevate their privileges.Credential Guard's virtual machine is very small and lightweight, running only a relatively simple process to manage credentials. Application Guard will go much further by running large parts of the Edge browser within a virtual machine.
This virtual machine won't, however, need a full operating system running inside it—just a minimal set of Windows features required to run the browser. Because Application Guard is running in a virtual machine it will have a much higher barrier between it and the host platform. It can't see other processes, it can't access local storage, it can't access any other installed applications, and, critically, it can't attack the kernel of the host system.In its first iteration, Application Guard will only be available for Edge.
Microsoft won't provide an API or let other applications use it. As with other VBS features, Application Guard will also only be available to users of Windows 10 Enterprise, with administrative control through group policies. Administrators will be able to mark some sites as trusted, and those sites won't use the virtual machine.
Admins also be able to control whether untrusted sites can use the clipboard or print.Microsoft recognizes that this feature would be desirable on consumer machines, too, and not just for Edge. Other browsers such as Chrome would also benefit from this kind of protection. So too would Office's 'Protected Mode' that's used for opening documents from untrusted sources.However, doing this has certain complexities. Currently, virtualized sites can't store persistent cookies, for example, because virtual machines get destroyed when the browser is closed. This may be acceptable for a locked-down enterprise environment, but it isn't a good fit for consumers.There are also compatibility constraints. VBS installs the Hyper-V hypervisor.
This requires a processor with hardware virtualization support, and it also requires I/O virtualization (such as Intel's VT-d) to protect against certain known attacks. This means that some systems in the wild won't support it.
There are also software concerns; only one hypervisor can be installed at a time, which means that a machine that's running Hyper-V cannot also run VMware Workstation or Virtual Box, say, or software that uses virtualization behind the scenes, such as the Bluestacks Android-on-Windows software.This virtualization also likely comes at some performance cost, although Microsoft is not saying just what that performance cost is right now.Nonetheless, this use of virtualization to harden a system is an exciting move. Experimental and special-use systems such as have used virtualization in a similar way, but are far from mainstream offerings. Microsoft is uniquely positioned take this kind of capability mainstream.Application Guard will become available later this year in Insider builds of Windows, hitting a stable version some time in 2017.
Getting started with Web-based accessNoMachine for the range allows you to access your remote desktop over the Web. This can be the physical desktop of a remote Windows, Mac, Linux and Raspberry host, on which you will need installed, or the virtual desktop of a remote Linux host on which you will need a product from the range installed. In both cases, there's no need for additional software on the device you are conncting from since all you need to connect securely to the remote server is an HTML-enabled Web browser. Read on to know how to access the physical desktop via the browser.If, on the other hand, you want to access your Linux virtual desktop, jump to the instructions. How to connect to the remote physical desktop via the browser You will need to check these three things first:. NoMachine Enterprise Desktop has to be installed on the remote host.
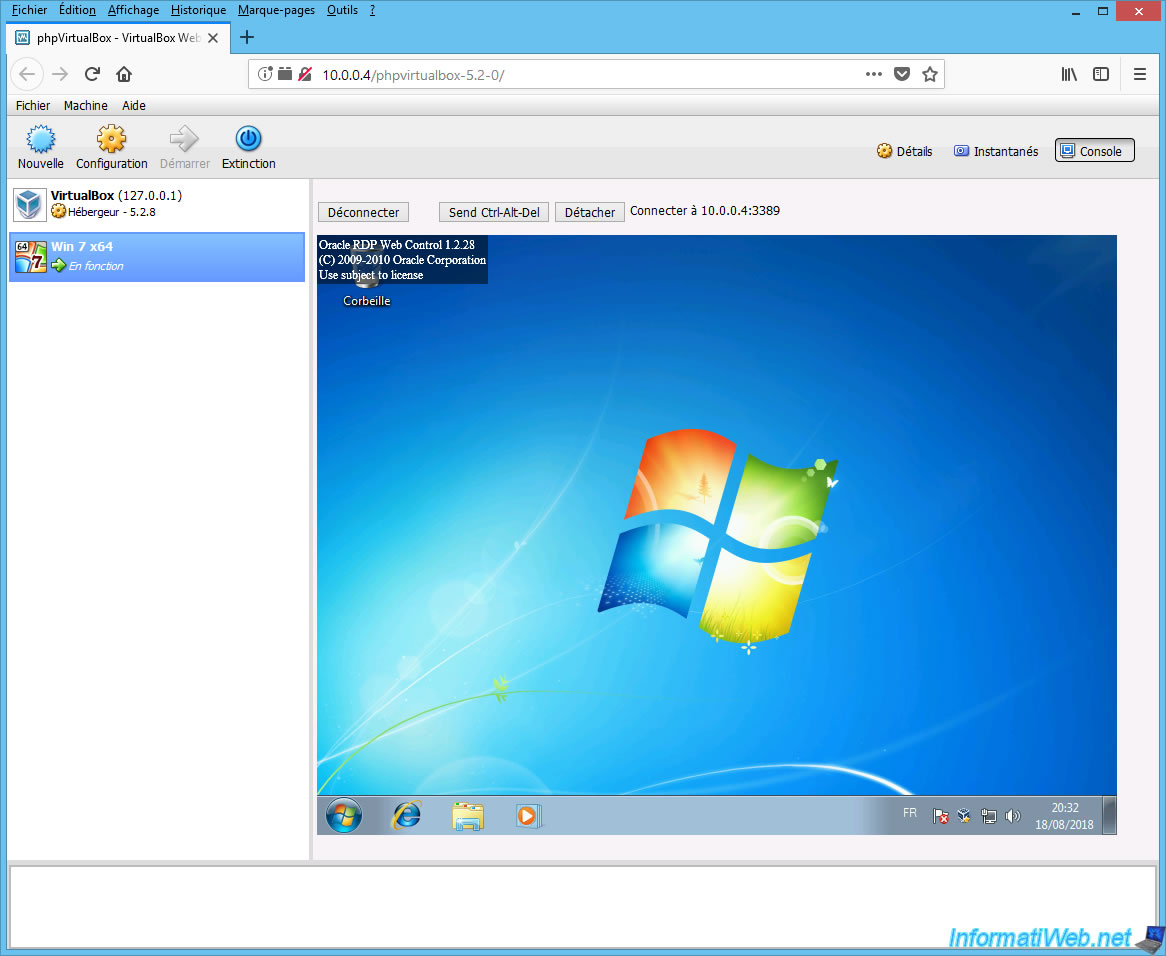
Once installed, Web access is already configured and ready to use out-of-the-box. For more details about installation and configuration, please see this guide.
You will need to know the IP address or hostname of the Enterprise Desktop server. Make sure you have account credentials to log in to your desktop.Step 1: Point your browser to the appropriate URLPoint your browser to where serverName is either the name or IP address of the host you want to reach (Fig. This address will be redirected to SSL and will appear as, for example,.
How to connect to a remote virtual desktop via the browserNoMachine’s Terminal Server range of products allows you to create and connect to virtual sessions over the Web. Virtual desktops and custom sessions (single applications run in the browser) are available only on Linux.There's no need for additional software on the local machine and all you need to connect securely to the remote host is a Web browser. You will need to check these three things first:.
Install any of the NoMachine products for Linux which support virtual desktops, the example below will use Workstation. Once installed, NoMachine is already configured and ready to use out-of-the-box.
Virtual Machine In Web Browser Software
For more details about installation and configuration of the Workstation, please see this guide. You will need to know the IP address or hostname of the Workstation host. Make sure you have account credentials to log in to your virtual Linux desktop.Step 1: Point your browser to the appropriate URLPoint your browser to or where serverName is either the name or IP address of the host you want to reach (Fig. This address will be redirected to SSL and will appear as, for example,.

2 - Insert your username and passwordStep 3: Select from the available session listAfter authenticating, the available session list will appear (Fig. 3) and provided you have installed one of the products from the Terminal Server range, you can create a new desktop session or connect to an already existing one from the list.
To create a new virtual desktop, click on the 'New desktop’ button in the top right corner. If you have a virtual desktop session already running (as in our example in Fig. 3 labelled as 'Default session on.' ), just double click on the icon of that session to re-connect.With NoMachine Terminal Server products, the physical display is made available only if you are the owner of that desktop, labelled as 'Physical display' in our example in Fig. To learn how to connect to the physical desktop via web, please see above.